This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies.
Harley-Davidson, Inc. (HOG) Q4 2024 Earnings ...
Feb 5, 2025 0
Ares Management Corporation (ARES) Q4 2024 Ea...
Feb 5, 2025 0
Harley-Davidson, Inc. (HOG) Q4 2024 Earnings ...
Feb 5, 2025 0
Ares Management Corporation (ARES) Q4 2024 Ea...
Feb 5, 2025 0











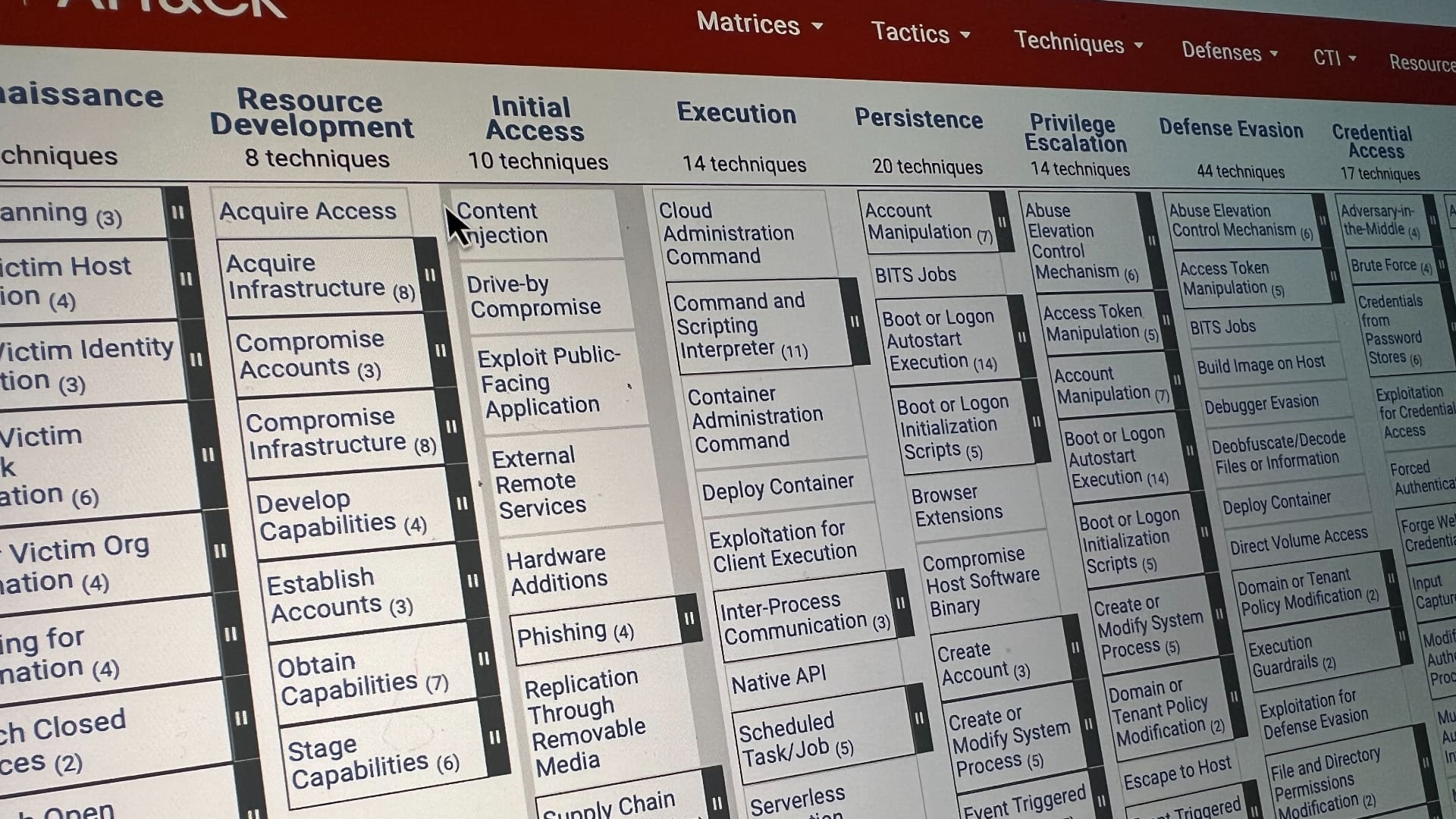
![How to Build Scalable Access Control for Your Web App [Full Handbook]](https://cdn.hashnode.com/res/hashnode/image/upload/v1738695897990/7a5962ce-9c4a-4e7c-bdeb-520dccc5d240.png?#)
























































_Elena_Uve_Alamy.jpg?#)