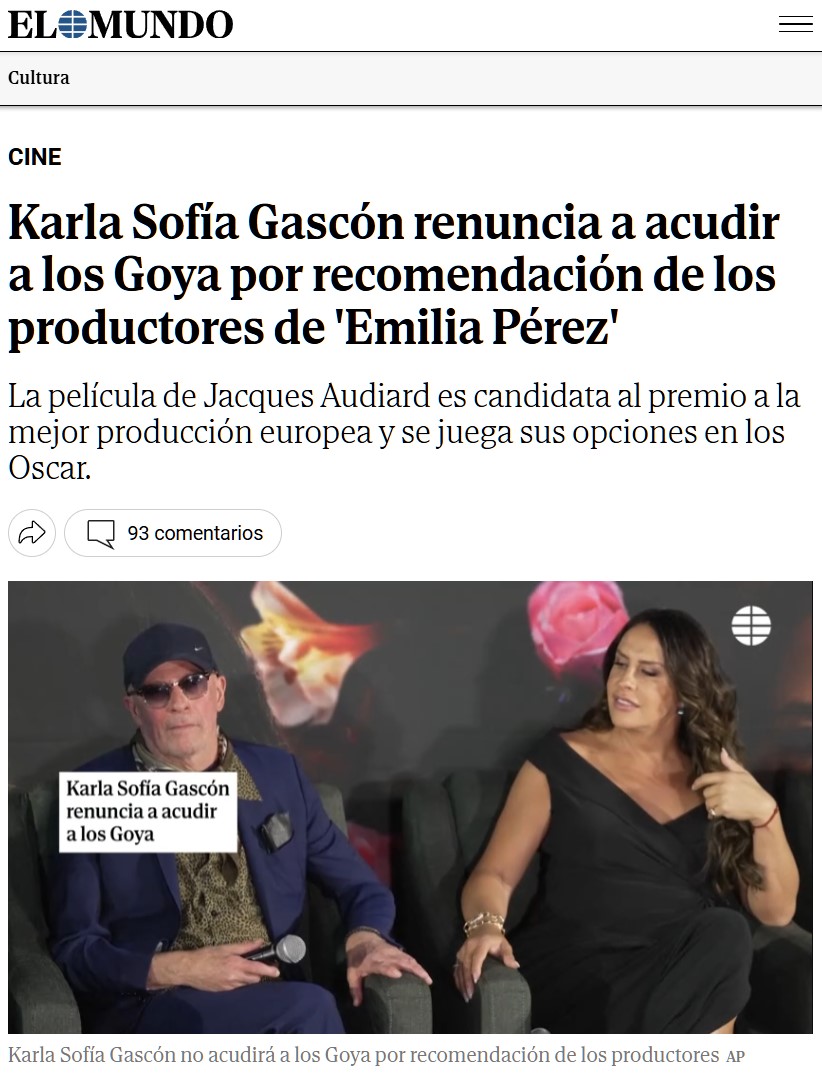
ExtractBitlockerKeys: extrae automáticamente claves de recuperación de Bitlocker de un dominio
Hoy os traemos una de esas herramientas que a todo red teamer le puede interesar tener en su arsenal: ExtractBitlockerKeys que, como su nombre indica, nos valdrá para extraer todas las claves de recuperación de Bitlocker... ¡de todas las máquinas de un dominio! Es decir, obtiene el listado / enumera las máquinas del dominio a través del controlador vía LDAP, hace su magia (filtro (objectClass=msFVE-RecoveryInformation)) y extrae la información (Computer FQDN, Domain, Recovery Key, Volume GUID, Created At y Organizational Units) a formato JSON, XLSX o SQLITE3.Ejemplo en Linux./ExtractBitlockerKeys.py -d 'domain.local' -u 'Administrator' -p 'Podalirius123!' --dc-ip 192.168.1.101Ejemplo en Windows.\ExtractBitlockerKeys.ps1 -dcip 192.168.1.101 -ExportToCSV ./keys.csv -ExportToJSON ./keys.jsonUso$ ./ExtractBitlockerKeys.py -hExtractBitlockerKeys.py v1.1 - by Remi GASCOU (Podalirius)usage: ExtractBitlockerKeys.py [-h] [-v] [-q] [-t THREADS] [--export-xlsx EXPORT_XLSX] [--export-json EXPORT_JSON] [--export-sqlite EXPORT_SQLITE] --dc-ip ip address [-d DOMAIN] [-u USER] [--no-pass | -p PASSWORD | -H [LMHASH:]NTHASH | --aes-key hex key] [-k]options: -h, --help show this help message and exit -v, --verbose Verbose mode. (default: False) -q, --quiet Show no information at all. -t THREADS, --threads THREADS Number of threads (default: 4).Output files: --export-xlsx EXPORT_XLSX Output XLSX file to store the results in. --export-json EXPORT_JSON Output JSON file to store the results in. --export-sqlite EXPORT_SQLITE Output SQLITE3 file to store the results in.Authentication & connection: --dc-ip ip address IP Address of the domain controller or KDC (Key Distribution Center) for Kerberos. If omitted it will use the domain part (FQDN) specified in the identity parameter -d DOMAIN, --domain DOMAIN (FQDN) domain to authenticate to -u USER, --user USER user to authenticate withCredentials: --no-pass Don't ask for password (useful for -k) -p PASSWORD, --password PASSWORD Password to authenticate with -H [LMHASH:]NTHASH, --hashes [LMHASH:]NTHASH NT/LM hashes, format is LMhash:NThash --aes-key hex key AES key to use for Kerberos Authentication (128 or 256 bits) -k, --kerberos Use Kerberos authentication. Grabs credentials from .ccache file (KRB5CCNAME) based on target parameters. If valid credentials cannot be found, it will use the ones specified in the command line.Proyecto: https://github.com/p0dalirius/ExtractBitlockerKeysReferencias:https://learn.microsoft.com/en-us/windows/win32/adschema/a-msfve-keypackagehttps://learn.microsoft.com/en-us/windows/win32/adschema/a-msfve-recoveryguidhttps://learn.microsoft.com/en-us/windows/win32/adschema/a-msfve-recoverypasswordhttps://learn.microsoft.com/en-us/windows/win32/adschema/a-msfve-volumeguid

Hoy os traemos una de esas herramientas que a todo red teamer le puede interesar tener en su arsenal: ExtractBitlockerKeys que, como su nombre indica, nos valdrá para extraer todas las claves de recuperación de Bitlocker... ¡de todas las máquinas de un dominio!
Es decir, obtiene el listado / enumera las máquinas del dominio a través del controlador vía LDAP, hace su magia (filtro (objectClass=msFVE-RecoveryInformation)) y extrae la información (Computer FQDN, Domain, Recovery Key, Volume GUID, Created At y Organizational Units) a formato JSON, XLSX o SQLITE3.
Ejemplo en Linux
./ExtractBitlockerKeys.py -d 'domain.local' -u 'Administrator' -p 'Podalirius123!' --dc-ip 192.168.1.101
Ejemplo en Windows
.\ExtractBitlockerKeys.ps1 -dcip 192.168.1.101 -ExportToCSV ./keys.csv -ExportToJSON ./keys.json
$ ./ExtractBitlockerKeys.py -hExtractBitlockerKeys.py v1.1 - by Remi GASCOU (Podalirius)usage: ExtractBitlockerKeys.py [-h] [-v] [-q] [-t THREADS] [--export-xlsx EXPORT_XLSX] [--export-json EXPORT_JSON] [--export-sqlite EXPORT_SQLITE] --dc-ip ip address [-d DOMAIN] [-u USER][--no-pass | -p PASSWORD | -H [LMHASH:]NTHASH | --aes-key hex key] [-k]options:-h, --help show this help message and exit-v, --verbose Verbose mode. (default: False)-q, --quiet Show no information at all.-t THREADS, --threads THREADSNumber of threads (default: 4).Output files:--export-xlsx EXPORT_XLSXOutput XLSX file to store the results in.--export-json EXPORT_JSONOutput JSON file to store the results in.--export-sqlite EXPORT_SQLITEOutput SQLITE3 file to store the results in.Authentication & connection:--dc-ip ip address IP Address of the domain controller or KDC (Key Distribution Center) for Kerberos. If omitted it will use the domain part (FQDN) specified in the identity parameter-d DOMAIN, --domain DOMAIN(FQDN) domain to authenticate to-u USER, --user USER user to authenticate withCredentials:--no-pass Don't ask for password (useful for -k)-p PASSWORD, --password PASSWORDPassword to authenticate with-H [LMHASH:]NTHASH, --hashes [LMHASH:]NTHASHNT/LM hashes, format is LMhash:NThash--aes-key hex key AES key to use for Kerberos Authentication (128 or 256 bits)-k, --kerberos Use Kerberos authentication. Grabs credentials from .ccache file (KRB5CCNAME) based on target parameters. If valid credentials cannot be found, it will use the ones specified in the command line.
- https://learn.microsoft.com/en-us/windows/win32/adschema/a-msfve-keypackage
- https://learn.microsoft.com/en-us/windows/win32/adschema/a-msfve-recoveryguid
- https://learn.microsoft.com/en-us/windows/win32/adschema/a-msfve-recoverypassword
- https://learn.microsoft.com/en-us/windows/win32/adschema/a-msfve-volumeguid